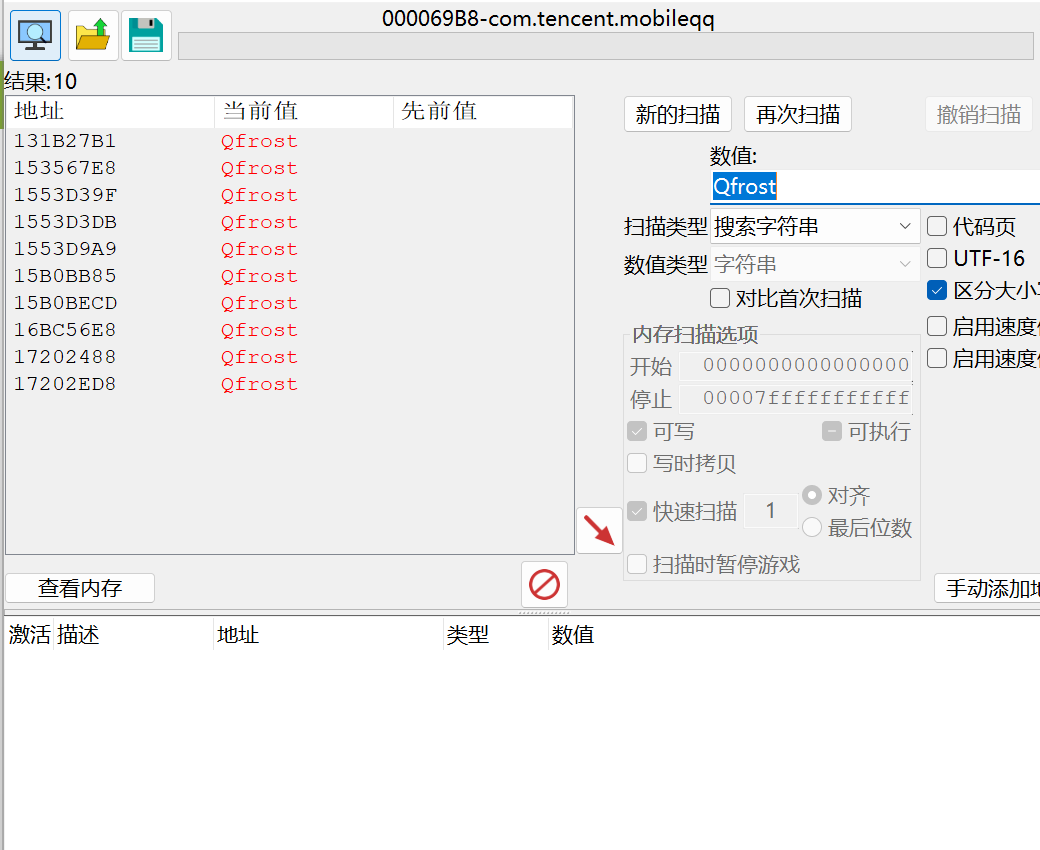
Sometimes, we have to face the situation where we need to read or write process memory but want the process to be completely unaware. In general, users can achieve this by utilizing the process_vm_readv and process_vm_writev syscalls provided from Android kernel. However, there are several methods to detect such malicious behaviors. Some anti-cheaters insert a type of special memory pages into the game’s memory, they can detect these memory pages being read or written by mincore. The detection mechanism is primarily based on the page fault interrupt. While the specific details of this detection principle are beyond the scope of this article, you can refer to additional resources if you are interested:
- https://blog.csdn.net/qq_30275375/article/details/123611213
- https://bbs.kanxue.com/thread-277144.htm
In order to access process’s memory without being detected, we need to find a as simple as possible way. One such approach is to utilize a kernel module for reading and writing phy memory. Thankfully, there are numerous open-source projects available that can be compiled and employed directly. In this artical, I will introduce a straightforward solution to compile and utilize a kernel module to access process’s memory.
Build Android Kernel
Before compiling the android kernel module, we must first compile the android kernel consistent with our phone to retrive header files. Such as the version of android kernel in my phone is 5.15.41, so I set branch to the common-android13-5.15

|
|
Build Kernel
LTO=thin BUILD_CONFIG=common/build.config.gki.aarch64 build/build.sh
// If you want to get kernel img with KernelSU, you can proceed to the following commands
curl -LSs "https://raw.githubusercontent.com/tiann/KernelSU/main/kernel/setup.sh" | bash -
LTO=thin BUILD_CONFIG=common/build.config.gki.aarch64 build/build.sh
Build rwMem Kernel Module
Once the kernel module is built, we can proceed to select an open-source project and compile it. I opted for the rwMem project, which offers a straightforward implementation for accessing physical memory. And @richar add hardware breakpoints feature to this project, and make this project support CheatEngine 7.5 version.
|
|
You will get rwMem.ko under the project root folder if you compile rwMem successfully.
We can use following commands to load the kernel module.
OP591BL1:/data/data/com.termux/files/home # insmod rwMem.ko
OP591BL1:/data/data/com.termux/files/home # lsmod | grep "rw"
rwMem 28672 0
Build CEServer
Defaultly, CheatEngine using process_vm_readv and process_vm_writev to access process memory. Now I want to use abilities providing from rwProcMem kernel module to read and write process memory by CheatEngine. It requires us to modify the source of CE-Server. Luckily, rwMem completes this work. It is very troublesome to build CE-Server on the computer, we must have environment allowing us cross compile Android programs. So I choose to compile CE-Server on my Android device.
Firstly, install termux. Copy rwMem/CEServer folders to your Android device.
|
|
We will obtain the result named a.out file in the current working directory. Running this program, the CE-Server will be started, and output the port of reverse proxy.
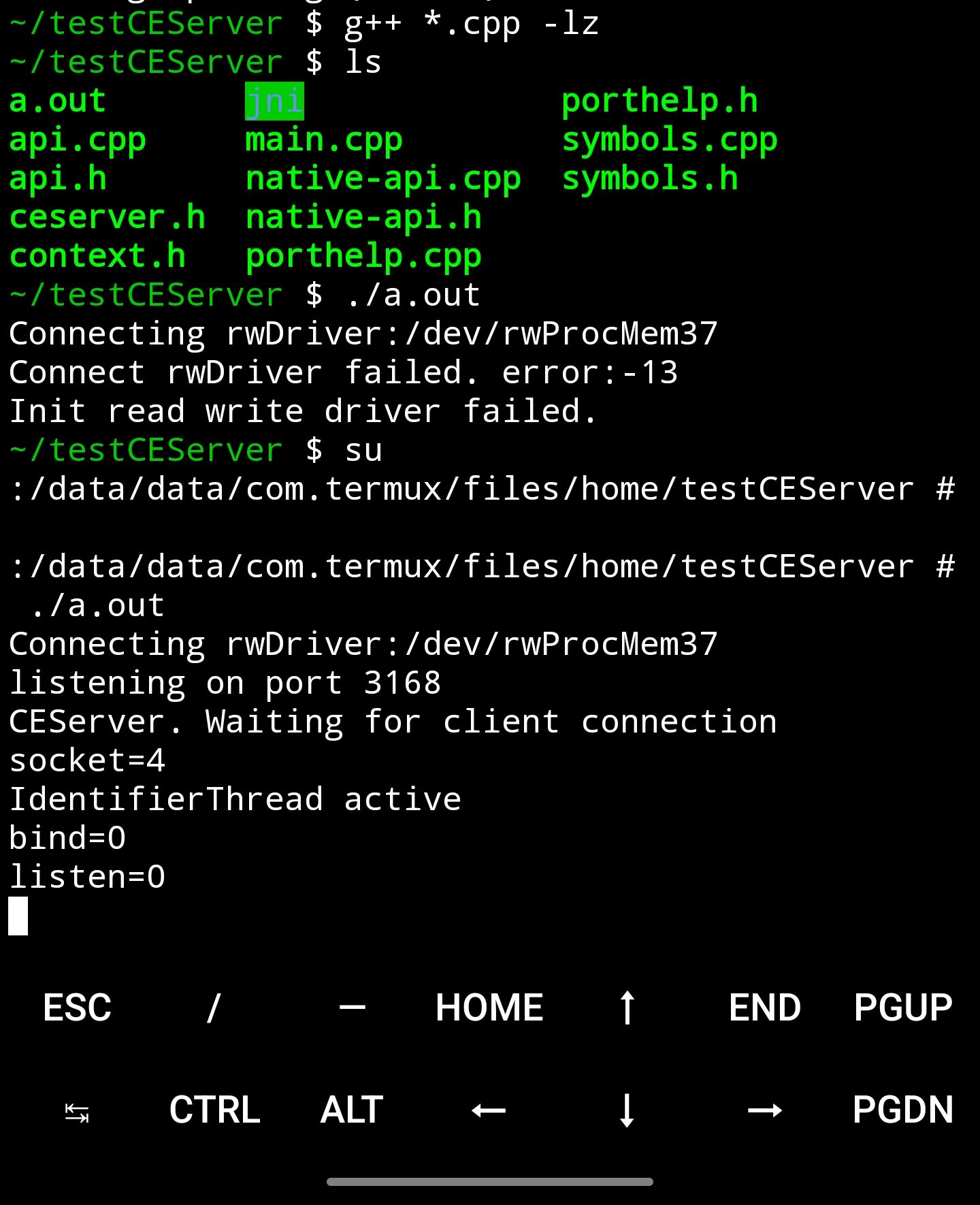
After getting this port, we can connect CE-Server using CheatEngine program.
|
|
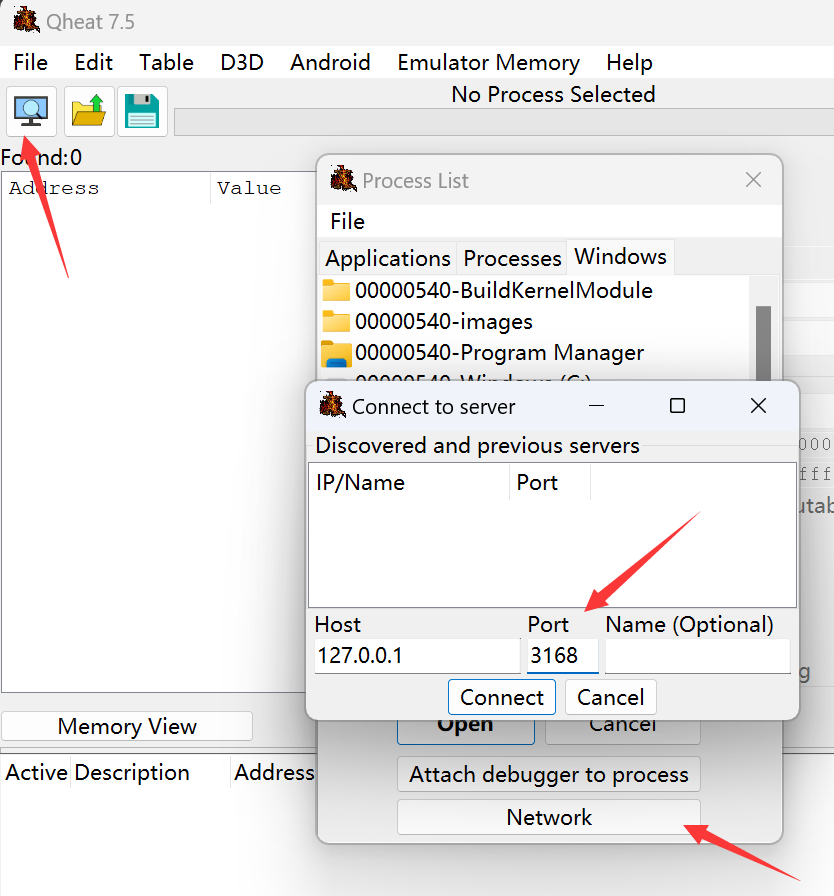
After waiting a few seconds, we will get process list of phone
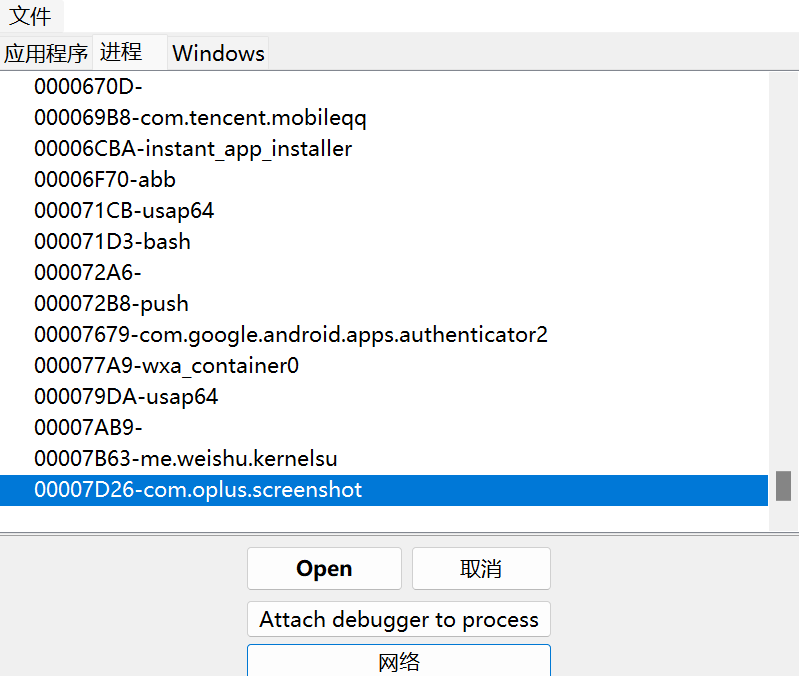
Okey, you can attach any processes and search what you want to get by CheatEngine using rwProcMem kernel module.